Adjusted Tests
Also fixed smaller issues in website.cljc. Better division of generate-common-*, now these functions may reside in c4k-common and generate standing ingresses/certs with only service and fqdn inputs (which need to be set anyways). Also moved predicates and specs to website.cljc.
This commit is contained in:
parent
d9e22a26ed
commit
a15b7b0d6f
8 changed files with 268 additions and 278 deletions
doc
src
main
cljc/dda/c4k_website
cljs/dda/c4k_website
resources/website
test/cljc/dda/c4k_website
BIN
doc/tryItOut.png
BIN
doc/tryItOut.png
Binary file not shown.
|
Before 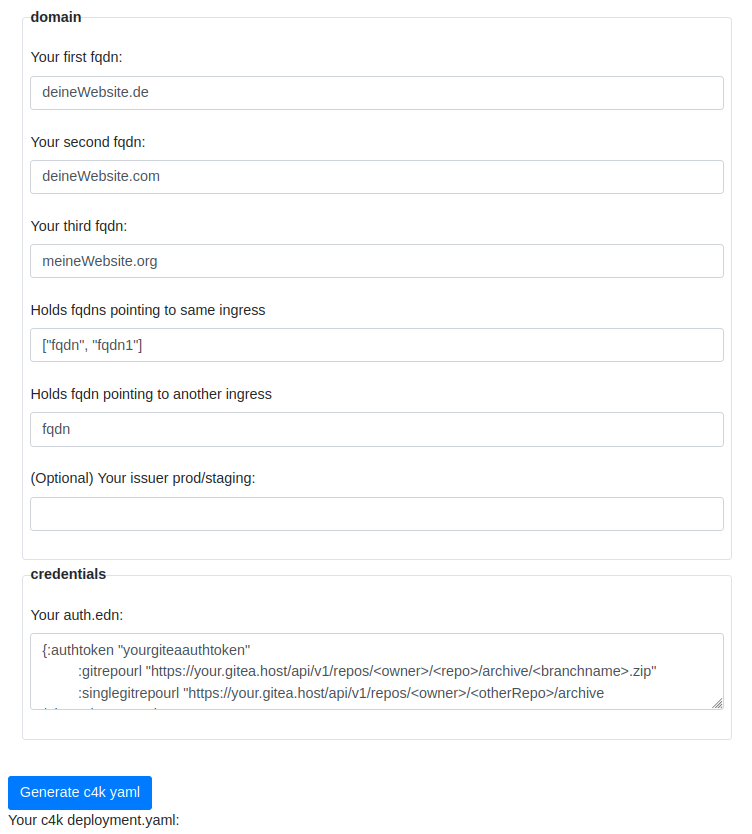
(image error) Size: 61 KiB After 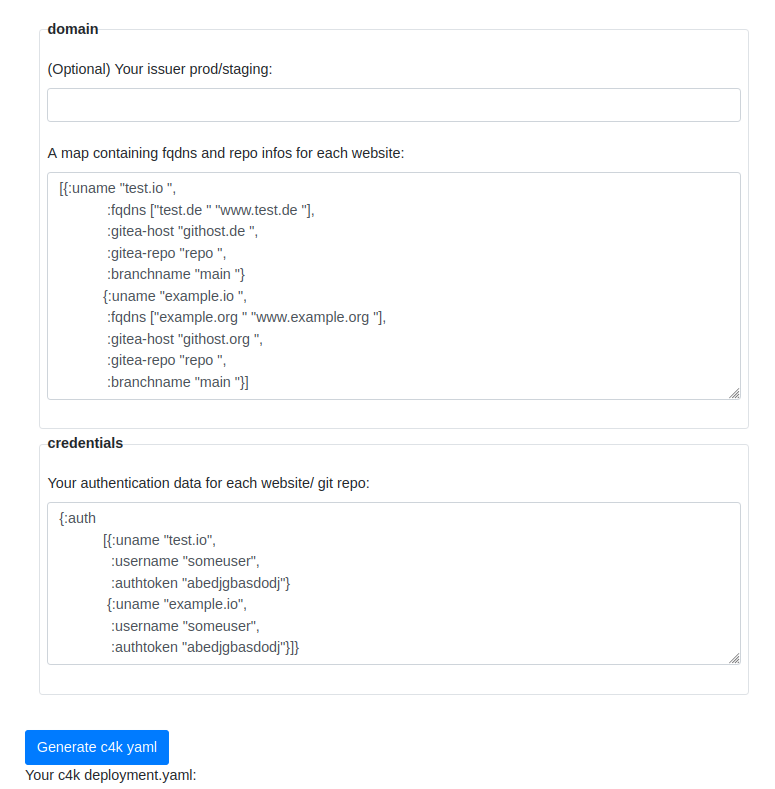
(image error) Size: 70 KiB 

|
|
|
@ -1,45 +1,16 @@
|
|||
(ns dda.c4k-website.core
|
||||
(:require
|
||||
[clojure.spec.alpha :as s]
|
||||
[dda.c4k-common.yaml :as yaml]
|
||||
[dda.c4k-common.common :as cm]
|
||||
[dda.c4k-website.website :as website]))
|
||||
(:require
|
||||
[clojure.spec.alpha :as s]
|
||||
[dda.c4k-common.yaml :as yaml]
|
||||
[dda.c4k-common.common :as cm]
|
||||
[dda.c4k-website.website :as website]))
|
||||
|
||||
(def config-defaults {:issuer "staging"})
|
||||
|
||||
(s/def ::websites vector?)
|
||||
(s/def ::auth vector?)
|
||||
|
||||
(def config? (s/keys :req-un [::websites]
|
||||
:opt-un [::website/issuer]))
|
||||
|
||||
(def auth? (s/keys :req-un [::auth]))
|
||||
|
||||
(defn flatten-and-reduce-config
|
||||
[config]
|
||||
(merge (-> config :websites first) (-> config :auth first) {:issuer (config :issuer)}))
|
||||
|
||||
(defn find-needle [needle haystack]
|
||||
;loop binds initial values once,
|
||||
;then binds values from each recursion call
|
||||
(loop [needle needle
|
||||
maybe-here haystack
|
||||
not-here '()]
|
||||
|
||||
(let [needle? (first maybe-here)]
|
||||
|
||||
;test for return or recur
|
||||
(if (or (= (str needle?) (str needle))
|
||||
(empty? maybe-here))
|
||||
|
||||
;return results
|
||||
[needle? maybe-here not-here]
|
||||
|
||||
;recur calls loop with new values
|
||||
(recur needle
|
||||
(rest maybe-here)
|
||||
(concat not-here (list (first maybe-here))))))))
|
||||
|
||||
(defn generate-configs [config]
|
||||
(loop [config config
|
||||
result []]
|
||||
|
|
|
|||
|
|
@ -12,40 +12,54 @@
|
|||
[dda.c4k-common.predicate :as pred]
|
||||
[clojure.string :as str]))
|
||||
|
||||
(defn keyword-string?
|
||||
[input]
|
||||
(str/starts-with? input "fqdn"))
|
||||
|
||||
(defn keyword-string-list?
|
||||
[input]
|
||||
(every? true? (map keyword-string? input)))
|
||||
|
||||
(defn fqdn-list?
|
||||
[input]
|
||||
(every? true? (map pred/fqdn-string? input)))
|
||||
|
||||
;(s/def ::uname pred/fqdn-string?)
|
||||
;(s/def ::issuer pred/letsencrypt-issuer?)
|
||||
;(s/def ::authtoken pred/bash-env-string?)
|
||||
;(s/def ::fqdns fqdn-list?)
|
||||
;(s/def ::gitea-host pred/fqdn-string?)
|
||||
;(s/def ::gitea-repo string?)
|
||||
;(s/def ::branchname string?)
|
||||
;(s/def ::username string?)
|
||||
(s/def ::uname pred/fqdn-string?)
|
||||
(s/def ::issuer pred/letsencrypt-issuer?)
|
||||
(s/def ::authtoken pred/bash-env-string?)
|
||||
(s/def ::fqdns fqdn-list?)
|
||||
(s/def ::gitea-host pred/fqdn-string?)
|
||||
(s/def ::gitea-repo string?)
|
||||
(s/def ::branchname string?)
|
||||
(s/def ::username string?)
|
||||
|
||||
;(def config? (s/keys :req-un [::uname ::fqdns ::gitea-host ::gitea-repo ::branchname]
|
||||
; :opt-un [::issuer]))
|
||||
(def websitedata? (s/keys :req-un [::uname ::fqdns ::gitea-host ::gitea-repo ::branchname]
|
||||
:opt-un [::issuer]))
|
||||
|
||||
;(def auth? (s/keys :req-un [::authtoken ::username]))
|
||||
(def websiteauth? (s/keys :req-un [::authtoken ::username]))
|
||||
|
||||
(s/def ::websites vector?)
|
||||
(s/def ::auth vector?)
|
||||
(defn auth-data-list?
|
||||
[input]
|
||||
(every? #(and
|
||||
(map? %)
|
||||
(and (s/valid? ::uname (% :uname)) (contains? % :uname))
|
||||
(and (s/valid? ::username (% :username)) (contains? % :username))
|
||||
(and (s/valid? ::authtoken (% :authtoken)) (contains? % :authtoken))) input))
|
||||
|
||||
(s/def ::auth auth-data-list?)
|
||||
|
||||
(def auth? (s/keys :req-un [::auth]))
|
||||
|
||||
(defn website-data-list?
|
||||
[input]
|
||||
(every? #(and
|
||||
(map? %)
|
||||
(and (s/valid? ::uname (% :uname)) (contains? % :uname))
|
||||
(and (s/valid? ::fqdns (% :fqdns)) (contains? % :fqdns))
|
||||
(and (s/valid? ::gitea-host (% :gitea-host)) (contains? % :gitea-host))
|
||||
(and (s/valid? ::gitea-repo (% :gitea-repo)) (contains? % :gitea-repo))
|
||||
(and (s/valid? ::branchname (% :branchname)) (contains? % :branchname))) input))
|
||||
|
||||
(defn websites? [input]
|
||||
(and (contains? input :websites) (website-data-list? (input :websites))) )
|
||||
|
||||
(s/def ::websites website-data-list?)
|
||||
|
||||
(def config? (s/keys :req-un [::websites]
|
||||
:opt-un [::issuer]))
|
||||
|
||||
(def auth? (s/keys :req-un [::auth]))
|
||||
|
||||
(def volume-size 3)
|
||||
|
||||
(defn unique-name-from-fqdn
|
||||
|
|
@ -60,6 +74,14 @@
|
|||
[uname]
|
||||
(str (unique-name-from-fqdn uname) "-cert"))
|
||||
|
||||
(defn generate-http-ingress-name
|
||||
[uname]
|
||||
(str (unique-name-from-fqdn uname) "-http-ingress"))
|
||||
|
||||
(defn generate-https-ingress-name
|
||||
[uname]
|
||||
(str (unique-name-from-fqdn uname) "-https-ingress"))
|
||||
|
||||
; https://your.gitea.host/api/v1/repos/<owner>/<repo>/archive/main.zip
|
||||
(defn make-gitrepourl
|
||||
[host repo user branch]
|
||||
|
|
@ -101,8 +123,8 @@
|
|||
(mapv #(assoc-in rule [:host] %) fqdns))
|
||||
|
||||
;create working ingress
|
||||
(defn-spec generate-common-http-ingress pred/map-or-seq?
|
||||
[config config?]
|
||||
(defn generate-common-http-ingress
|
||||
[config]
|
||||
(let [{:keys [fqdn service-name]} config]
|
||||
(->
|
||||
(yaml/load-as-edn "website/http-ingress.yaml")
|
||||
|
|
@ -110,17 +132,13 @@
|
|||
(cm/replace-all-matching-values-by-new-value "FQDN" fqdn))))
|
||||
|
||||
(defn-spec generate-website-http-ingress pred/map-or-seq?
|
||||
[config config?]
|
||||
[config websitedata?]
|
||||
(let [{:keys [uname fqdns]} config
|
||||
fqdn (first fqdns)
|
||||
spec-rules [:spec :rules]
|
||||
service-name (generate-service-name uname)]
|
||||
spec-rules [:spec :rules]]
|
||||
(->
|
||||
(generate-common-http-ingress
|
||||
{:fqdn fqdn :service-name service-name})
|
||||
(assoc-in
|
||||
[:metadata :name]
|
||||
(str (unique-name-from-fqdn uname) "-http-ingress"))
|
||||
{:fqdn (first fqdns) :service-name (generate-service-name uname)})
|
||||
(cm/replace-all-matching-values-by-new-value "c4k-common-http-ingress" (generate-http-ingress-name uname))
|
||||
(#(assoc-in %
|
||||
spec-rules
|
||||
(make-host-rules-from-fqdns
|
||||
|
|
@ -128,61 +146,49 @@
|
|||
fqdns))))))
|
||||
|
||||
;create working ingress
|
||||
(defn-spec generate-common-https-ingress pred/map-or-seq?
|
||||
[config config?]
|
||||
(let [{:keys [fqdn service-name cert-name]} config]
|
||||
(defn generate-common-https-ingress
|
||||
[config]
|
||||
(let [{:keys [fqdn service-name]} config]
|
||||
(->
|
||||
(yaml/load-as-edn "website/https-ingress.yaml")
|
||||
(cm/replace-all-matching-values-by-new-value "SERVICENAME" service-name)
|
||||
(cm/replace-all-matching-values-by-new-value "CERTNAME" cert-name)
|
||||
(cm/replace-all-matching-values-by-new-value "SERVICENAME" service-name)
|
||||
(cm/replace-all-matching-values-by-new-value "FQDN" fqdn))))
|
||||
|
||||
(defn-spec generate-website-https-ingress pred/map-or-seq?
|
||||
[config config?]
|
||||
[config websitedata?]
|
||||
(let [{:keys [uname fqdns]} config
|
||||
fqdn (first fqdns)
|
||||
spec-rules [:spec :rules]
|
||||
spec-tls-hosts [:spec :tls 0 :hosts]
|
||||
service-name (generate-service-name uname)
|
||||
cert-name (generate-cert-name uname)]
|
||||
spec-tls-hosts [:spec :tls 0 :hosts]]
|
||||
(->
|
||||
(generate-common-https-ingress
|
||||
{:fqdn fqdn :service-name service-name :cert-name cert-name})
|
||||
(assoc-in
|
||||
[:metadata :name]
|
||||
(str (unique-name-from-fqdn uname) "-https-ingress"))
|
||||
(#(assoc-in %
|
||||
spec-tls-hosts
|
||||
fqdns))
|
||||
(#(assoc-in %
|
||||
spec-rules
|
||||
(make-host-rules-from-fqdns
|
||||
(-> % :spec :rules first) ;get first ingress rule
|
||||
fqdns))))))
|
||||
{:fqdn (first fqdns) :service-name (generate-service-name uname)})
|
||||
(cm/replace-all-matching-values-by-new-value "c4k-common-https-ingress" (generate-https-ingress-name uname))
|
||||
(cm/replace-all-matching-values-by-new-value "c4k-common-cert" (generate-cert-name uname))
|
||||
(#(assoc-in % spec-tls-hosts fqdns))
|
||||
(#(assoc-in % spec-rules (make-host-rules-from-fqdns (-> % :spec :rules first) fqdns))))))
|
||||
|
||||
(defn-spec generate-common-certificate pred/map-or-seq?
|
||||
[config config?]
|
||||
(let [{:keys [uname fqdns issuer]
|
||||
(defn generate-common-certificate
|
||||
[config]
|
||||
(let [{:keys [fqdn issuer]
|
||||
:or {issuer "staging"}} config
|
||||
fqdn (first fqdns)
|
||||
letsencrypt-issuer (name issuer)
|
||||
cert-name (generate-cert-name uname)]
|
||||
letsencrypt-issuer (name issuer)]
|
||||
(->
|
||||
(yaml/load-as-edn "website/certificate.yaml")
|
||||
(assoc-in [:spec :issuerRef :name] letsencrypt-issuer)
|
||||
(cm/replace-all-matching-values-by-new-value "CERTNAME" cert-name)
|
||||
(assoc-in [:spec :issuerRef :name] letsencrypt-issuer)
|
||||
(cm/replace-all-matching-values-by-new-value "FQDN" fqdn))))
|
||||
|
||||
(defn-spec generate-website-certificate pred/map-or-seq?
|
||||
[config config?]
|
||||
(let [{:keys [fqdns]} config
|
||||
[config websitedata?]
|
||||
(let [{:keys [uname issuer fqdns]} config
|
||||
spec-dnsNames [:spec :dnsNames]]
|
||||
(->
|
||||
(generate-common-certificate config)
|
||||
(generate-common-certificate
|
||||
{:issuer issuer, :fqdn (first fqdns)})
|
||||
(cm/replace-all-matching-values-by-new-value "c4k-common-cert" (generate-cert-name uname))
|
||||
(assoc-in spec-dnsNames fqdns))))
|
||||
|
||||
(defn-spec generate-nginx-configmap pred/map-or-seq?
|
||||
[config config?]
|
||||
[config websitedata?]
|
||||
(let [{:keys [uname fqdns]} config]
|
||||
(->
|
||||
(yaml/load-as-edn "website/nginx-configmap.yaml")
|
||||
|
|
@ -193,21 +199,21 @@
|
|||
(-> % :data :website.conf) #"FQDN" (str (str/join " " fqdns) ";")))))))
|
||||
|
||||
(defn-spec generate-nginx-deployment pred/map-or-seq?
|
||||
[config config?]
|
||||
[config websitedata?]
|
||||
(let [{:keys [uname]} config]
|
||||
(->
|
||||
(yaml/load-as-edn "website/nginx-deployment.yaml")
|
||||
(replace-all-matching-subvalues-in-string-start "NAME" (unique-name-from-fqdn uname)))))
|
||||
|
||||
(defn-spec generate-nginx-service pred/map-or-seq?
|
||||
[config config?]
|
||||
[config websitedata?]
|
||||
(let [{:keys [uname]} config]
|
||||
(->
|
||||
(yaml/load-as-edn "website/nginx-service.yaml")
|
||||
(replace-all-matching-subvalues-in-string-start "NAME" (unique-name-from-fqdn uname)))))
|
||||
|
||||
(defn-spec generate-website-content-volume pred/map-or-seq?
|
||||
[config config?]
|
||||
[config websitedata?]
|
||||
(let [{:keys [uname]} config]
|
||||
(->
|
||||
(yaml/load-as-edn "website/website-content-volume.yaml")
|
||||
|
|
@ -215,21 +221,21 @@
|
|||
(cm/replace-all-matching-values-by-new-value "WEBSITESTORAGESIZE" (str (str volume-size) "Gi")))))
|
||||
|
||||
(defn-spec generate-website-build-cron pred/map-or-seq?
|
||||
[config config?]
|
||||
[config websitedata?]
|
||||
(let [{:keys [uname]} config]
|
||||
(->
|
||||
(yaml/load-as-edn "website/website-build-cron.yaml")
|
||||
(replace-all-matching-subvalues-in-string-start "NAME" (unique-name-from-fqdn uname)))))
|
||||
|
||||
(defn-spec generate-website-build-deployment pred/map-or-seq?
|
||||
[config config?]
|
||||
[config websitedata?]
|
||||
(let [{:keys [uname]} config]
|
||||
(->
|
||||
(yaml/load-as-edn "website/website-build-deployment.yaml")
|
||||
(replace-all-matching-subvalues-in-string-start "NAME" (unique-name-from-fqdn uname)))))
|
||||
|
||||
(defn-spec generate-website-build-secret pred/map-or-seq?
|
||||
[auth auth?]
|
||||
[auth websiteauth?]
|
||||
(let [{:keys [uname
|
||||
authtoken
|
||||
gitea-host
|
||||
|
|
|
|||
|
|
@ -29,21 +29,32 @@
|
|||
(generate-group
|
||||
"domain"
|
||||
(cm/concat-vec
|
||||
(br/generate-input-field "fqdn" "Your first fqdn:" "deineWebsite.de")
|
||||
(br/generate-input-field "fqdn1" "Your second fqdn:" "deineWebsite.com")
|
||||
(br/generate-input-field "fqdn2" "Your third fqdn:" "meineWebsite.org")
|
||||
(br/generate-input-field "multi" "Holds fqdns pointing to same ingress" "[\"fqdn\", \"fqdn1\"]")
|
||||
(br/generate-input-field "single" "Holds fqdn pointing to another ingress" "fqdn")
|
||||
(br/generate-input-field "issuer" "(Optional) Your issuer prod/staging:" "")))
|
||||
(br/generate-input-field "issuer" "(Optional) Your issuer prod/staging:" "")
|
||||
(br/generate-text-area
|
||||
"websites" "A map containing fqdns and repo infos for each website:"
|
||||
"[{:uname \"test.io \",
|
||||
:fqdns [\"test.de \" \"www.test.de \"],
|
||||
:gitea-host \"githost.de \",
|
||||
:gitea-repo \"repo \",
|
||||
:branchname \"main \"}
|
||||
{:uname \"example.io \",
|
||||
:fqdns [\"example.org \" \"www.example.org \"],
|
||||
:gitea-host \"githost.org \",
|
||||
:gitea-repo \"repo \",
|
||||
:branchname \"main \"}]"
|
||||
"10")))
|
||||
(generate-group
|
||||
"credentials"
|
||||
(br/generate-text-area
|
||||
"auth" "Your auth.edn:"
|
||||
"{:authtoken \"yourgiteaauthtoken\"
|
||||
:gitrepourl \"https://your.gitea.host/api/v1/repos/<owner>/<repo>/archive/<branchname>.zip\"
|
||||
:singlegitrepourl \"https://your.gitea.host/api/v1/repos/<owner>/<otherRepo>/archive/<branchname>.zip\"
|
||||
}"
|
||||
"3"))
|
||||
"auth" "Your authentication data for each website/ git repo:"
|
||||
"{:auth
|
||||
[{:uname \"test.io\",
|
||||
:username \"someuser\",
|
||||
:authtoken \"abedjgbasdodj\"}
|
||||
{:uname \"example.io\",
|
||||
:username \"someuser\",
|
||||
:authtoken \"abedjgbasdodj\"}]}"
|
||||
"7"))
|
||||
[(br/generate-br)]
|
||||
(br/generate-button "generate-button" "Generate c4k yaml")))]
|
||||
(br/generate-output "c4k-website-output" "Your c4k deployment.yaml:" "15")))
|
||||
|
|
@ -58,25 +69,20 @@
|
|||
(defn config-from-document []
|
||||
(let [issuer (br/get-content-from-element "issuer" :optional true)]
|
||||
(merge
|
||||
{:fqdn (br/get-content-from-element "fqdn")}
|
||||
{:websites (br/get-content-from-element "websites" :deserializer edn/read-string)}
|
||||
(when (not (st/blank? issuer))
|
||||
{:issuer issuer}))))
|
||||
|
||||
(defn validate-all! []
|
||||
(br/validate! "fqdn" ::website/fqdn)
|
||||
(br/validate! "fqdn1" ::website/fqdn1)
|
||||
(br/validate! "fqdn2" ::website/fqdn2)
|
||||
(br/validate! "single" ::website/single)
|
||||
(br/validate! "multi" ::website/multi)
|
||||
(br/validate! "websites" ::website/websites)
|
||||
(br/validate! "issuer" ::website/issuer :optional true)
|
||||
(br/validate! "auth" core/auth? :deserializer edn/read-string)
|
||||
(br/validate! "auth" website/auth? :deserializer edn/read-string)
|
||||
(br/set-form-validated!))
|
||||
|
||||
(defn add-validate-listener [name]
|
||||
(-> (br/get-element-by-id name)
|
||||
(.addEventListener "blur" #(do (validate-all!)))))
|
||||
|
||||
|
||||
(defn init []
|
||||
(br/append-hickory (generate-content-div))
|
||||
(-> js/document
|
||||
|
|
@ -89,10 +95,6 @@
|
|||
core/config-defaults
|
||||
core/k8s-objects)
|
||||
(br/set-output!)))))
|
||||
(add-validate-listener "fqdn")
|
||||
(add-validate-listener "fqdn1")
|
||||
(add-validate-listener "fqdn2")
|
||||
(add-validate-listener "single")
|
||||
(add-validate-listener "multi")
|
||||
(add-validate-listener "websites")
|
||||
(add-validate-listener "issuer")
|
||||
(add-validate-listener "auth"))
|
||||
|
|
|
|||
|
|
@ -1,10 +1,10 @@
|
|||
apiVersion: cert-manager.io/v1
|
||||
kind: Certificate
|
||||
metadata:
|
||||
name: CERTNAME
|
||||
name: c4k-common-cert
|
||||
namespace: default
|
||||
spec:
|
||||
secretName: CERTNAME
|
||||
secretName: c4k-common-cert
|
||||
commonName: FQDN
|
||||
duration: 2160h # 90d
|
||||
renewBefore: 360h # 15d
|
||||
|
|
|
|||
|
|
@ -1,7 +1,7 @@
|
|||
apiVersion: networking.k8s.io/v1
|
||||
kind: Ingress
|
||||
metadata:
|
||||
name: http-ingress
|
||||
name: c4k-common-http-ingress
|
||||
namespace: default
|
||||
annotations:
|
||||
traefik.ingress.kubernetes.io/router.entrypoints: web
|
||||
|
|
|
|||
|
|
@ -1,7 +1,7 @@
|
|||
apiVersion: networking.k8s.io/v1
|
||||
kind: Ingress
|
||||
metadata:
|
||||
name: https-ingress-gitea
|
||||
name: c4k-common-https-ingress
|
||||
namespace: default
|
||||
annotations:
|
||||
traefik.ingress.kubernetes.io/router.entrypoints: websecure
|
||||
|
|
@ -10,7 +10,7 @@ spec:
|
|||
tls:
|
||||
- hosts:
|
||||
- FQDN
|
||||
secretName: CERTNAME
|
||||
secretName: c4k-common-cert
|
||||
rules:
|
||||
- host: FQDN
|
||||
http:
|
||||
|
|
|
|||
|
|
@ -8,96 +8,111 @@
|
|||
[dda.c4k-website.website :as cut]
|
||||
[dda.c4k-website.core :as cutc]))
|
||||
|
||||
(st/instrument `cut/generate-single-certificate)
|
||||
(st/instrument `cut/generate-single-ingress)
|
||||
(st/instrument `cut/generate-single-nginx-configmap)
|
||||
(st/instrument `cut/generate-multi-certificate)
|
||||
(st/instrument `cut/generate-multi-ingress)
|
||||
(st/instrument `cut/generate-multi-nginx-configmap)
|
||||
(st/instrument `cut/generate-http-ingress)
|
||||
(st/instrument `cut/generate-https-ingress)
|
||||
(st/instrument `cut/generate-nginx-configmap)
|
||||
(st/instrument `cut/generate-nginx-deployment)
|
||||
(st/instrument `cut/generate-nginx-service)
|
||||
(st/instrument `cut/generate-website-content-volume)
|
||||
(st/instrument `cut/generate-website-certificate)
|
||||
(st/instrument `cut/generate-website-build-cron)
|
||||
(st/instrument `cut/generate-website-build-deployment)
|
||||
(st/instrument `cut/generate-website-build-secret)
|
||||
|
||||
(deftest should-generate-certificate
|
||||
(is (= {:name-c2 "prod", :name-c1 "staging"}
|
||||
(th/map-diff (cut/generate-single-certificate {:fqdn "test.de"
|
||||
:fqdn1 "test.org"
|
||||
:single "fqdn1"
|
||||
:fqdn2 "bla.com"
|
||||
:multi ["fqdn1", "fqdn"]})
|
||||
(cut/generate-single-certificate {:fqdn "test.com"
|
||||
:fqdn1 "test.org"
|
||||
:issuer "prod"
|
||||
:single "fqdn1"
|
||||
:fqdn2 "bla.com"
|
||||
:multi ["fqdn1", "fqdn"]})))))
|
||||
|
||||
(deftest should-generate-ingress
|
||||
(deftest should-generate-http-ingress
|
||||
(is (= {:apiVersion "networking.k8s.io/v1",
|
||||
:kind "Ingress",
|
||||
:metadata
|
||||
{:name "test-de-ingress",
|
||||
{:name "test-io-http-ingress",
|
||||
:namespace "default",
|
||||
:annotations
|
||||
{:ingress.kubernetes.io/ssl-redirect "true",
|
||||
:traefik.ingress.kubernetes.io/router.middlewares "default-redirect-https@kubernetescrd"}},
|
||||
#:traefik.ingress.kubernetes.io{:router.entrypoints "web",
|
||||
:router.middlewares "default-redirect-https@kubernetescrd"}},
|
||||
:spec
|
||||
{:tls [{:hosts ["test.de"], :secretName "test-de-cert"}],
|
||||
:rules
|
||||
{:rules
|
||||
[{:host "test.de",
|
||||
:http {:paths [{:pathType "Prefix", :path "/", :backend {:service {:name "test-de-service", :port {:number 80}}}}]}}]}}
|
||||
(cut/generate-single-ingress {:fqdn "test.de"
|
||||
:fqdn1 "test.org"
|
||||
:fqdn2 "bla.com"
|
||||
:multi ["fqdn1", "fqdn"]
|
||||
:single "fqdn"}))))
|
||||
:http
|
||||
{:paths [{:pathType "Prefix", :path "/", :backend {:service {:name "test-io-service", :port {:number 80}}}}]}}
|
||||
{:host "www.test.de",
|
||||
:http
|
||||
{:paths [{:pathType "Prefix", :path "/", :backend {:service {:name "test-io-service", :port {:number 80}}}}]}}
|
||||
{:host "test-it.de",
|
||||
:http
|
||||
{:paths [{:pathType "Prefix", :path "/", :backend {:service {:name "test-io-service", :port {:number 80}}}}]}}
|
||||
{:host "www.test-it.de",
|
||||
:http
|
||||
{:paths [{:pathType "Prefix", :path "/", :backend {:service {:name "test-io-service", :port {:number 80}}}}]}}]}}
|
||||
(cut/generate-website-http-ingress {:uname "test.io"
|
||||
:fqdns ["test.de" "www.test.de" "test-it.de" "www.test-it.de"]}))))
|
||||
|
||||
(deftest should-generate-ingress
|
||||
(deftest should-generate-https-ingress
|
||||
(is (= {:apiVersion "networking.k8s.io/v1",
|
||||
:kind "Ingress",
|
||||
:metadata
|
||||
{:name "test-de-ingress",
|
||||
{:name "test-io-https-ingress",
|
||||
:namespace "default",
|
||||
:annotations
|
||||
{:ingress.kubernetes.io/ssl-redirect "true",
|
||||
:traefik.ingress.kubernetes.io/router.middlewares "default-redirect-https@kubernetescrd"}},
|
||||
:annotations #:traefik.ingress.kubernetes.io{:router.entrypoints "websecure", :router.tls "true"}},
|
||||
:spec
|
||||
{:tls [{:hosts ["test.de"], :secretName "test-de-cert"}],
|
||||
{:tls [{:hosts ["test.de" "www.test.de" "test-it.de" "www.test-it.de"], :secretName "test-io-cert"}],
|
||||
:rules
|
||||
[{:host "test.de",
|
||||
:http {:paths [{:pathType "Prefix", :path "/", :backend {:service {:name "test-de-service", :port {:number 80}}}}]}}]}}
|
||||
(cut/generate-single-ingress {:fqdn "test.de"
|
||||
:fqdn1 "test.org"
|
||||
:fqdn2 "bla.com"
|
||||
:multi ["fqdn1", "fqdn"]
|
||||
:single "fqdn"}))))
|
||||
:http
|
||||
{:paths [{:pathType "Prefix", :path "/", :backend {:service {:name "test-io-service", :port {:number 80}}}}]}}
|
||||
{:host "www.test.de",
|
||||
:http
|
||||
{:paths [{:pathType "Prefix", :path "/", :backend {:service {:name "test-io-service", :port {:number 80}}}}]}}
|
||||
{:host "test-it.de",
|
||||
:http
|
||||
{:paths [{:pathType "Prefix", :path "/", :backend {:service {:name "test-io-service", :port {:number 80}}}}]}}
|
||||
{:host "www.test-it.de",
|
||||
:http
|
||||
{:paths [{:pathType "Prefix", :path "/", :backend {:service {:name "test-io-service", :port {:number 80}}}}]}}]}}
|
||||
(cut/generate-website-https-ingress {:uname "test.io"
|
||||
:fqdns ["test.de" "www.test.de" "test-it.de" "www.test-it.de"]}))))
|
||||
|
||||
(deftest should-generate-website-certificate
|
||||
(is (= {:name-c1 "prod", :name-c2 "staging"}
|
||||
(th/map-diff (cut/generate-website-certificate {:uname "test.io"
|
||||
:gitea-host "gitea.evilorg"
|
||||
:gitea-repo "none"
|
||||
:branchname "mablain"
|
||||
:issuer "prod"
|
||||
:fqdns ["test.org" "test.de"]})
|
||||
(cut/generate-website-certificate {:uname "test.io"
|
||||
:gitea-host "gitea.evilorg"
|
||||
:gitea-repo "none"
|
||||
:branchname "mablain"
|
||||
:issuer "staging"
|
||||
:fqdns ["test.org" "test.de"]})))))
|
||||
|
||||
(deftest should-generate-nginx-configmap
|
||||
(is (= {:website.conf-c1 "server {\n listen 80 default_server;\n listen [::]:80 default_server;\n listen 443 ssl;\n ssl_certificate /etc/certs/tls.crt;\n ssl_certificate_key /etc/certs/tls.key;\n server_name test.de; \n add_header Strict-Transport-Security 'max-age=31536000; includeSubDomains; preload';\n add_header Content-Security-Policy \"default-src 'self'; font-src *;img-src * data:; script-src *; style-src *\";\n add_header X-XSS-Protection \"1; mode=block\";\n add_header X-Frame-Options \"SAMEORIGIN\";\n add_header X-Content-Type-Options nosniff;\n add_header Referrer-Policy \"strict-origin\";\n # add_header Permissions-Policy \"permissions here\";\n root /var/www/html/website/;\n index index.html;\n location / {\n try_files $uri $uri/ /index.html =404;\n }\n}\n",
|
||||
:website.conf-c2 "server {\n listen 80 default_server;\n listen [::]:80 default_server;\n listen 443 ssl;\n ssl_certificate /etc/certs/tls.crt;\n ssl_certificate_key /etc/certs/tls.key;\n server_name test.com; \n add_header Strict-Transport-Security 'max-age=31536000; includeSubDomains; preload';\n add_header Content-Security-Policy \"default-src 'self'; font-src *;img-src * data:; script-src *; style-src *\";\n add_header X-XSS-Protection \"1; mode=block\";\n add_header X-Frame-Options \"SAMEORIGIN\";\n add_header X-Content-Type-Options nosniff;\n add_header Referrer-Policy \"strict-origin\";\n # add_header Permissions-Policy \"permissions here\";\n root /var/www/html/website/;\n index index.html;\n location / {\n try_files $uri $uri/ /index.html =404;\n }\n}\n",
|
||||
:name-c1 "test-de-configmap",
|
||||
:name-c2 "test-com-configmap"}
|
||||
(th/map-diff (cut/generate-single-nginx-configmap {:fqdn "test.de"
|
||||
:fqdn1 "test.org"
|
||||
:single "fqdn"
|
||||
:fqdn2 "bla.com"
|
||||
:multi ["fqdn1", "fqdn"]})
|
||||
(cut/generate-single-nginx-configmap {:fqdn "test.org"
|
||||
:fqdn1 "test.com"
|
||||
:single "fqdn1"
|
||||
:fqdn2 "bla.com"
|
||||
:multi ["fqdn1", "fqdn"]})))))
|
||||
(is (= {:website.conf-c1 "server {\n listen 80 default_server;\n listen [::]:80 default_server;\n listen 443 ssl;\n ssl_certificate /etc/certs/tls.crt;\n ssl_certificate_key /etc/certs/tls.key;\n server_name test.de www.test.de test-it.de www.test-it.de; \n add_header Strict-Transport-Security 'max-age=31536000; includeSubDomains; preload';\n add_header Content-Security-Policy \"default-src 'self'; font-src *;img-src * data:; script-src *; style-src *\";\n add_header X-XSS-Protection \"1; mode=block\";\n add_header X-Frame-Options \"SAMEORIGIN\";\n add_header X-Content-Type-Options nosniff;\n add_header Referrer-Policy \"strict-origin\";\n # add_header Permissions-Policy \"permissions here\";\n root /var/www/html/website/;\n index index.html;\n location / {\n try_files $uri $uri/ /index.html =404;\n }\n}\n",
|
||||
:website.conf-c2 "server {\n listen 80 default_server;\n listen [::]:80 default_server;\n listen 443 ssl;\n ssl_certificate /etc/certs/tls.crt;\n ssl_certificate_key /etc/certs/tls.key;\n server_name example.de www.example.de example-by.de www.example-by.de; \n add_header Strict-Transport-Security 'max-age=31536000; includeSubDomains; preload';\n add_header Content-Security-Policy \"default-src 'self'; font-src *;img-src * data:; script-src *; style-src *\";\n add_header X-XSS-Protection \"1; mode=block\";\n add_header X-Frame-Options \"SAMEORIGIN\";\n add_header X-Content-Type-Options nosniff;\n add_header Referrer-Policy \"strict-origin\";\n # add_header Permissions-Policy \"permissions here\";\n root /var/www/html/website/;\n index index.html;\n location / {\n try_files $uri $uri/ /index.html =404;\n }\n}\n",
|
||||
:name-c1 "test-io-configmap",
|
||||
:name-c2 "example-io-configmap"}
|
||||
(th/map-diff (cut/generate-nginx-configmap {:uname "test.io",
|
||||
:gitea-host "gitea.evilorg",
|
||||
:gitea-repo "none",
|
||||
:branchname "mablain",
|
||||
:fqdns ["test.de" "www.test.de" "test-it.de" "www.test-it.de"]})
|
||||
(cut/generate-nginx-configmap {:uname "example.io",
|
||||
:gitea-host "gitea.evilorg",
|
||||
:gitea-repo "none",
|
||||
:branchname "mablain",
|
||||
:fqdns ["example.de" "www.example.de" "example-by.de" "www.example-by.de"]})))))
|
||||
|
||||
(deftest should-generate-nginx-deployment
|
||||
(is (= {:apiVersion "apps/v1",
|
||||
:kind "Deployment",
|
||||
:metadata {:name "test-de-deployment"},
|
||||
:metadata {:name "test-io-deployment"},
|
||||
:spec
|
||||
{:replicas 1,
|
||||
:selector {:matchLabels {:app "test-de-nginx"}},
|
||||
:selector {:matchLabels {:app "test-io-nginx"}},
|
||||
:template
|
||||
{:metadata {:labels {:app "test-de-nginx"}},
|
||||
{:metadata {:labels {:app "test-io-nginx"}},
|
||||
:spec
|
||||
{:containers
|
||||
[{:name "test-de-nginx",
|
||||
[{:name "test-io-nginx",
|
||||
:image "nginx:latest",
|
||||
:imagePullPolicy "IfNotPresent",
|
||||
:ports [{:containerPort 80}],
|
||||
|
|
@ -109,42 +124,42 @@
|
|||
:volumes
|
||||
[{:name "nginx-config-volume",
|
||||
:configMap
|
||||
{:name "test-de-configmap",
|
||||
{:name "test-io-configmap",
|
||||
:items
|
||||
[{:key "nginx.conf", :path "nginx.conf"}
|
||||
{:key "website.conf", :path "conf.d/website.conf"}
|
||||
{:key "mime.types", :path "mime.types"}]}}
|
||||
{:name "log", :emptyDir {}}
|
||||
{:name "website-content-volume", :persistentVolumeClaim {:claimName "test-de-content-volume"}}
|
||||
{:name "website-content-volume", :persistentVolumeClaim {:claimName "test-io-content-volume"}}
|
||||
{:name "website-cert",
|
||||
:secret
|
||||
{:secretName "test-de-cert", :items [{:key "tls.crt", :path "tls.crt"} {:key "tls.key", :path "tls.key"}]}}]}}}}
|
||||
(cut/generate-nginx-deployment {:fqdn "test.de"
|
||||
:fqdn1 "test.com"
|
||||
:fqdn2 "test.io"
|
||||
:single "fqdn2"
|
||||
:multi ["fqdn1", "fqdn2"]}))))
|
||||
{:secretName "test-io-cert", :items [{:key "tls.crt", :path "tls.crt"} {:key "tls.key", :path "tls.key"}]}}]}}}}
|
||||
(cut/generate-nginx-deployment {:uname "test.io",
|
||||
:gitea-host "gitea.evilorg",
|
||||
:gitea-repo "none",
|
||||
:branchname "mablain",
|
||||
:fqdns ["test.de" "www.test.de" "test-it.de" "www.test-it.de"]}))))
|
||||
|
||||
(deftest should-generate-nginx-service
|
||||
(is (= {:name-c1 "test-de-service",
|
||||
:name-c2 "test-com-service",
|
||||
:app-c1 "test-de-nginx",
|
||||
:app-c2 "test-com-nginx"}
|
||||
(th/map-diff (cut/generate-nginx-service (cutc/set-multi-fqdn {:fqdn "test.de"
|
||||
:fqdn1 "bla.de"
|
||||
:fqdn2 "bla.com"
|
||||
:single "fqdn1"
|
||||
:multi ["fqdn", "fqdn"]}))
|
||||
(cut/generate-nginx-service (cutc/set-multi-fqdn {:fqdn "test.com"
|
||||
:fqdn1 "bla.de"
|
||||
:fqdn2 "bla.com"
|
||||
:single "fqdn1"
|
||||
:multi ["fqdn", "fqdn"]}))))))
|
||||
(is (= {:name-c1 "test-io-service",
|
||||
:name-c2 "test-org-service",
|
||||
:app-c1 "test-io-nginx",
|
||||
:app-c2 "test-org-nginx"}
|
||||
(th/map-diff (cut/generate-nginx-service {:uname "test.io",
|
||||
:gitea-host "gitea.evilorg",
|
||||
:gitea-repo "none",
|
||||
:branchname "mablain",
|
||||
:fqdns ["test.de" "www.test.de" "test-it.de" "www.test-it.de"]})
|
||||
(cut/generate-nginx-service {:uname "test.org",
|
||||
:gitea-host "gitea.evilorg",
|
||||
:gitea-repo "none",
|
||||
:branchname "mablain",
|
||||
:fqdns ["test.de" "www.test.de" "test-it.de" "www.test-it.de"]})))))
|
||||
|
||||
(deftest should-generate-website-build-cron
|
||||
(is (= {:apiVersion "batch/v1beta1",
|
||||
:kind "CronJob",
|
||||
:metadata {:name "test-de-build-cron", :labels {:app.kubernetes.part-of "website"}},
|
||||
:metadata {:name "test-io-build-cron", :labels {:app.kubernetes.part-of "website"}},
|
||||
:spec
|
||||
{:schedule "1,7,14,21,28,35,42,49,54,59 * * * *",
|
||||
:successfulJobsHistoryLimit 1,
|
||||
|
|
@ -155,81 +170,77 @@
|
|||
{:spec
|
||||
{:containers
|
||||
[{:image "domaindrivenarchitecture/c4k-website-build",
|
||||
:name "test-de-build-app",
|
||||
:name "test-io-build-app",
|
||||
:imagePullPolicy "IfNotPresent",
|
||||
:command ["/entrypoint.sh"],
|
||||
:envFrom [{:secretRef {:name "test-de-secret"}}],
|
||||
:command ["/entrypoint.sh"],
|
||||
:envFrom [{:secretRef {:name "test-io-secret"}}],
|
||||
:volumeMounts [{:name "content-volume", :mountPath "/var/www/html/website"}]}],
|
||||
:volumes [{:name "content-volume", :persistentVolumeClaim {:claimName "test-de-content-volume"}}],
|
||||
:volumes [{:name "content-volume", :persistentVolumeClaim {:claimName "test-io-content-volume"}}],
|
||||
:restartPolicy "OnFailure"}}}}}}
|
||||
(cut/generate-website-build-cron {:fqdn "test.de"
|
||||
:fqdn1 "bla.de"
|
||||
:fqdn2 "bla.com"
|
||||
:single "fqdn1"
|
||||
:multi ["fqdn1", "fqdn"]}))))
|
||||
(cut/generate-website-build-cron {:uname "test.io",
|
||||
:gitea-host "gitea.evilorg",
|
||||
:gitea-repo "none",
|
||||
:branchname "mablain",
|
||||
:fqdns ["test.de" "www.test.de" "test-it.de" "www.test-it.de"]}))))
|
||||
|
||||
(deftest should-generate-website-build-deployment
|
||||
(is (= {:apiVersion "apps/v1",
|
||||
:kind "Deployment",
|
||||
:metadata {:name "test-de-build-deployment"},
|
||||
:metadata {:name "test-io-build-deployment"},
|
||||
:spec
|
||||
{:replicas 0,
|
||||
:selector {:matchLabels {:app "test-de-builder"}},
|
||||
:selector {:matchLabels {:app "test-io-builder"}},
|
||||
:strategy {:type "Recreate"},
|
||||
:template
|
||||
{:metadata
|
||||
{:labels {:app "test-de-builder", :app.kubernetes.io/name "test-de-builder", :app.kubernetes.io/part-of "website"}},
|
||||
{:labels {:app "test-io-builder", :app.kubernetes.io/name "test-io-builder", :app.kubernetes.io/part-of "website"}},
|
||||
:spec
|
||||
{:containers
|
||||
[{:image "domaindrivenarchitecture/c4k-website-build",
|
||||
:name "test-de-build-app",
|
||||
:name "test-io-build-app",
|
||||
:imagePullPolicy "IfNotPresent",
|
||||
:command ["/entrypoint.sh"],
|
||||
:envFrom [{:secretRef {:name "test-de-secret"}}],
|
||||
:command ["/entrypoint.sh"],
|
||||
:envFrom [{:secretRef {:name "test-io-secret"}}],
|
||||
:volumeMounts [{:name "content-volume", :mountPath "/var/www/html/website"}]}],
|
||||
:volumes [{:name "content-volume", :persistentVolumeClaim {:claimName "test-de-content-volume"}}]}}}}
|
||||
(cut/generate-website-build-deployment {:fqdn "test.de"
|
||||
:fqdn1 "bla.de"
|
||||
:fqdn2 "bla.com"
|
||||
:single "fqdn1"
|
||||
:multi ["fqdn1", "fqdn"]}))))
|
||||
:volumes [{:name "content-volume", :persistentVolumeClaim {:claimName "test-io-content-volume"}}]}}}}
|
||||
(cut/generate-website-build-deployment {:uname "test.io",
|
||||
:gitea-host "gitea.evilorg",
|
||||
:gitea-repo "none",
|
||||
:branchname "mablain",
|
||||
:fqdns ["test.de" "www.test.de" "test-it.de" "www.test-it.de"]}))))
|
||||
|
||||
(deftest should-generate-website-build-secret
|
||||
(is (= {:name-c1 "test-de-secret",
|
||||
:name-c2 "test-com-secret",
|
||||
:AUTHTOKEN-c1 (b64/encode "token1"),
|
||||
(is (= {:name-c1 "test-io-secret",
|
||||
:name-c2 "test-org-secret",
|
||||
:AUTHTOKEN-c1 (b64/encode "token1"),
|
||||
:AUTHTOKEN-c2 (b64/encode "token2"),
|
||||
:GITREPOURL-c1 (b64/encode "test.de/user/repo.git"),
|
||||
:GITREPOURL-c2 (b64/encode "test.com/user/repo.git")}
|
||||
(th/map-diff (cut/generate-website-build-secret {:fqdn "test.de"
|
||||
:fqdn1 "bla.de"
|
||||
:fqdn2 "bla.com"
|
||||
:single "fqdn1"
|
||||
:multi ["fqdn1", "fqdn"]
|
||||
:authtoken "token1"
|
||||
:gitrepourl "test.de/user/repo.git"
|
||||
:singlegitrepourl "test.com/user/otherrepo.git"})
|
||||
(cut/generate-website-build-secret {:fqdn "test.com"
|
||||
:fqdn1 "bla.de"
|
||||
:fqdn2 "bla.com"
|
||||
:single "fqdn1"
|
||||
:multi ["fqdn1", "fqdn"]
|
||||
:authtoken "token2"
|
||||
:gitrepourl "test.com/user/repo.git"
|
||||
:singlegitrepourl "test.com/user/otherrepo.git"})))))
|
||||
:GITREPOURL-c1 (b64/encode "https://gitlab.org/api/v1/repos/dumpty/websitebau/archive/testname.zip"),
|
||||
:GITREPOURL-c2 (b64/encode "https://github.com/api/v1/repos/humpty/websitedachs/archive/testname.zip")}
|
||||
(th/map-diff (cut/generate-website-build-secret {:uname "test.io",
|
||||
:authtoken "token1",
|
||||
:gitea-host "gitlab.org",
|
||||
:gitea-repo "websitebau",
|
||||
:username "dumpty",
|
||||
:branchname "testname"})
|
||||
(cut/generate-website-build-secret {:uname "test.org",
|
||||
:authtoken "token2",
|
||||
:gitea-host "github.com",
|
||||
:gitea-repo "websitedachs",
|
||||
:username "humpty",
|
||||
:branchname "testname"})))))
|
||||
|
||||
(deftest should-generate-website-content-volume
|
||||
(is (= {:name-c1 "test-de-content-volume",
|
||||
:name-c2 "test-com-content-volume",
|
||||
:app-c1 "test-de-nginx",
|
||||
:app-c2 "test-com-nginx"}
|
||||
(th/map-diff (cut/generate-website-content-volume {:fqdn "test.de"
|
||||
:fqdn1 "bla.de"
|
||||
:fqdn2 "bla.com"
|
||||
:single "fqdn1"
|
||||
:multi ["fqdn1", "fqdn"]})
|
||||
(cut/generate-website-content-volume {:fqdn "test.com"
|
||||
:fqdn1 "bla.de"
|
||||
:fqdn2 "bla.com"
|
||||
:single "fqdn1"
|
||||
:multi ["fqdn1", "fqdn"]})))))
|
||||
(is (= {:name-c1 "test-io-content-volume",
|
||||
:name-c2 "test-org-content-volume",
|
||||
:app-c1 "test-io-nginx",
|
||||
:app-c2 "test-org-nginx"}
|
||||
(th/map-diff (cut/generate-website-content-volume {:uname "test.io",
|
||||
:gitea-host "gitea.evilorg",
|
||||
:gitea-repo "none",
|
||||
:branchname "mablain",
|
||||
:fqdns ["test.de" "www.test.de" "test-it.de" "www.test-it.de"]})
|
||||
(cut/generate-website-content-volume {:uname "test.org",
|
||||
:gitea-host "gitea.evilorg",
|
||||
:gitea-repo "none",
|
||||
:branchname "mablain",
|
||||
:fqdns ["test.de" "www.test.de" "test-it.de" "www.test-it.de"]})))))
|
||||
|
|
|
|||
Loading…
Add table
Reference in a new issue